Android is the most popular operating system for handhelds, and among virus makers it ranks second in popularity, after Windows. The first malware for Android appeared in 2010.
Because Android is an open source operating system that enjoys worldwide popularity and enables users to install applications from any source, most malicious programs are designed to infect this platform.
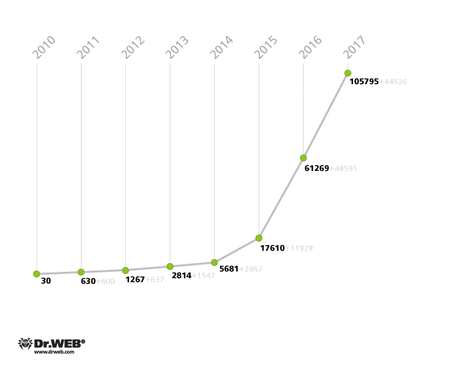
This graph shows how the number of entries for Android malware in the Dr.Web database has grown over time
Growth in the number of entries in 2014—102%!
Since 2010 the number of entries has increased 189 times
By April 1, 2015, the number of signatures in the Dr.Web database for Android reached almost 9,000.
In just the first three months of 2015, the database expanded by more than 25%!
Also, bear in mind that one Dr.Web signature facilitates the detection of more than one malicious program.
Most malicious programs for Android are designed with THEFT in mind.
Mobile devices are equipped with a wide range of features, and the makers of Android malware steal everything that can be stolen from a mobile device:
- Money—from a mobile account, an online banking system or a bank card
- Logins and passwords used for online banking and electronic payment systems, social networking sites, etc.
- SMS messages
- Calls
- Emails
- Pictures — these can be used to blackmail users or damage their reputation by publishing them on the Internet
- Records of the device owner's negotiations even if the device owner did not engage in negotiations; the malware can do this on the owner’s behalf
- Phone book contact information
- Location data
- Any kind of technical information about the device (IMEI/IMSI/SID, mobile phone number, OS version, SDK version, device model, and information about the device's manufacturer)
In many cases, users themselves download and install malware on their mobile devices!

For example, Android.Plankton, which collects and transmits information about infected devices to criminals, was loaded by users manually from Google Play (originally Android Market) over 150,000 times (!) before it was removed from the catalogue by the portal's administration.
Statistics provided by Dr.Web for Android show that approximately 50% of users enable the option for installing applications from unknown sources (i.e., not from Google Play). This means that users can install malicious applications downloaded from a forum or any other questionable site.
Social engineering techniques enable criminals to spread malware onto handhelds on a massive scale. For example, more than 30,000 South Korean Android device owners downloaded the banking TrojanAndroid.SmsBot.75.origin while trying to track the fate of a “postal delivery”.
Most users are absolutely confident that they can spot the actions of a Trojan horse on their mobile device.
A good Trojan is one that the user will never notice.
Virus writers learnt this a long time ago.
The activities of the most successful Trojan thieves can only be discovered after everything has already been stolen.
For example, to reduce the likelihood that users will detect its unwanted activities, the dialler Android.Dialer.7.origin disables the earpiece of the mobile device during unsolicited phone calls, and to remove all traces of its activities, it also clears the system log and call list of all the information that can help expose it.
Trojans that steal money from mobile accounts by subscribing users to paid services are also able to keep a low profile very well. Normally subscribing users to chargeable services involves a confirmation message which is sent when the operation is successfully completed. Trojans hide these SMS so that users don’t catch on to them too soon. Some malware can automatically send SMS containing a verification code to complete the authorization process for paid services — these messages are often intercepted and hidden by Trojans too.
Many "advanced" Trojans are disguised as legitimate software, but as soon as they are launched, they remove their icon and run in the background so that users won't notice them.
Attackers also embed Trojans in Android firmware and make them an integral part of the operating system. These ”guerrillas” enjoy elevated permissions and can covertly perform the widest range of unwanted activities.
To avoid being detected by anti-viruses, some Trojans come with features that enable them to neutralise security software: anti-viruses can be blocked or completely removed from a device.
Banking Trojans
These are malicious programs for Android that are designed to steal money from bank cards and online payment systems.

Mobile banking is indeed convenient. Many banks offer their customers online banking applications for Android. These are used not only by private individuals but also by companies. As a rule, this feature is used by employees who are authorised to conduct transactions.
Money is the primary target of attacks on handhelds.
Android.BankBot.33.originCan perform the following malicious tasks:
The victim can remain in the dark about the theft for some time because Android.BankBot.33.origin can intercept and block SMS notifications about transactions. |

|
Users install this Trojan horse themselves (for this to happen, installation from third-party sources must be enabled in the system settings)!
From January till April 2015, this Trojan was detected by Dr.Web for Android 62,840 times which accounts for 0.37% of the total number of threats identified during this period.
Android.SpyEye.1

|
Should a user of a desktop or laptop go to a bank site whose address is on the invading Trojan’s list, the malware will inject text or web forms into the loaded page to lure the user into divulging their account access credentials. An unsuspecting victim loads a bank page in their browser to access their account and discovers that the bank has introduced new security measures with which they must comply in order to use the online banking client. They are also prompted to download an update for the client program—this update contains this Trojan horse. This program intercepts and forwards to the attackers one-time online banking passwords which are delivered with short messages. |
Android.BankBot.21.origin
| In order to get hold of bank card information and steal money, Android.BankBot.21.origin checks whether a Google Play application window is active, and, if it is, the malware will imitate the web form used to associate a bank card with a user account. The divulged information is transmitted to the attackers' server. The rest is quite simple. |

|
Android.BankBot.29.origin

|
The Trojan tries to acquire administrator permissions on the device by concealing the corresponding system prompt behind its dialogue box, so that the user is very likely to grant the requested permissions to the application. After that, stealing the money is a cakewalk. |
Stealing incoming SMS
You probably think that a stolen short message is not a really big deal. Well, that all depends on why the stolen SMS was sent to your phone.

Which short messages containing sensitive financial information do Trojans steal?
- SMS confirmations and requests related to subscriptions to premium services. They are stolen to make sure that the victim remains unaware of the subscription for as long as possible and doesn't do anything to disrupt the Trojan’s operation.
- Verification messages from online banking systems; the messages contain mTAN codes.
Stolen SMS are forwarded to a command and control server owned by the attackers. This trick is used by malicious programs belonging to several families.
Stealing money by sending SMS
For example, Android.SmsSend Trojans transfer money from a mobile account to criminals by sending premium messages from compromised devices.
According to statistics aggregated by Dr.Web for Android, in 2014 Android.SmsSend programs were detected 20,223,854 times.
Android.SmsBot malware can also send, intercept and delete SMS.
Statistics provided by Dr.Web for Android show that Android.SmsBot programs were detected 5,985,063 times in 2014.
Stealing money by calling premium numbers
Dialers are a family of Trojans for Android that covertly makes calls to premium numbers. This way of generating a profit is also rather popular among virus makers.
In 2014, Dr.Web for Android detected Android.Dialer programs 177,397 times.
Stealing contact information
Although this doesn't sound like much of a problem, there is also money to be made here. Information about any actual contact can be sold, and there are several categories of buyers.
Spammers
Spam is a thriving business. And it's not just about sending mass spam mailings of harmless ads.
Sending bulk SMS containing malware download links is now one of the most popular ways to distribute Android threats.
For example, Android.Wormle.1.origin can be spread with SMS messages that are sent to all the contacts found in a compromised device’s phone book. By the end of November 2014, Android.Wormle.1.origin managed to infect more than 15,000 Android handhelds in about 30 countries.
Phishers
They collect contact information to send those contacts emails containing links to bogus sites that appear to belong to legitimate banks or payment processors. If the contact who receives the email does go to such a site, a phisher may trick them into providing their online banking login and password or bank card information. Confident that they have gotten onto a legitimate site, users enter all the requested information into the web form voluntarily.
Criminals mounting DDoS attacks
These individuals need contact information to infect mobile devices and use it in DDoS attacks on various sites, e.g., those belonging to their customer's competitors.
Spies
(secret services and competitors). Every contact is a godsend for a spy or blackmailer. Also, people spying on you can read your correspondence, record your conversations and upload your photos to a remote server.
For example, Android.Spy.130.origin sends intruders details on SMS correspondence, outgoing calls, and the device's location and can also secretly call a specified number, thus turning the smart phone or tablet into a covert listening device.
Growth in the number of Android.Spy malware definitions in the Dr.Web virus database

You actively use
- Google Play
- Google Play Music
- Gmail
- Viber
- Skype
- «ВКонтакте»
- «Одноклассники»
- Twitter…?
Criminals can make use of all your data—to sell it or blackmail you
Dr.Web for Android protects against mobile theft
Protection components for Android
Anti-virus
Will protect your system from Trojans and other malware.Anti-theft
Will help you find your mobile device if it has been lost or stolen, and, if necessary, wipe confidential information from the device remotely.Anti-spam
Will shield your device from unwanted calls and SMS messages.Cloud-based URL filter
Will help you avoid unwanted Internet sites even if your Dr.Web for Android’s virus definitions are outdated.Firewall
Controls application network activityThe Security Auditor
Troubleshoots the device to identify security problems and offers solutions to address them.
The free license for Dr.Web for Android Light only includes the anti-virus; other components are absent.
Dr.Web for Android free download
| Google Play | apk installer | QR code |
Use Dr.Web for Android Comprehensive Protection free of charge!
If you have a commercial license for
| Dr.Web Security Space |
(an electronic license or a boxed product).
The number of free licenses provided to you for your mobile devices is equal to the number of PCs covered by your purchased license.
You don’t have a Dr.Web license yet? That’s easy to fix!
Thank you for taking the time to read through the text.